Russia’s likely interference in elections in Ukraine can develop in three vectors. One is the traditional technology with handouts and bribes for voters, carousel voting and other ways to affect the results. They are not purely Russian methods. All elections in Ukraine have shown plenty of domestic experts in this illegal cause. The sorry state of Ukraine’s economy pushes people to accept this manipulation in pursuit of extra income.
The second vector includes attempts to influence people through information. It is normal to look for candidates’ skeletons in the closet in every election. There is hardly a vote without scandals and sensational revelations anywhere in the world. However, the latest campaign in the U.S. showed how important it is to differentiate between hunts for compromising information and determined interference to damage one political force or candidate and benefit another. The channels for this communication are selected based on the features of the target groups: for some, a free newspaper distributed at a metro station is enough; others prefer Facebook posts, while some have to be bombarded with endless political talk shows on TV. Information varies, too, from simple slogans “for all things good and against all things bad” or cheap manipulations comparing life in the past to that in the present, to more exquisite ones with hand-picked experts that look like they provide objective and unbiased statistics, which then proves to have little in common with reliable sources or reality.
Artificial ideological polarization into homeboys and strangers is another popular approach. It is used by everyone, from populists to more reasonable politicians. It always leads to a similar result: delivered through the right channels and in the right words, this information helps change the voters’ preferences – sometimes to a complete opposite. Manipulators will especially focus on those Ukrainians that have not yet made their choice (see p. 18). This is easier than trying to persuade people with a shaped mindset. The authorities will do little to stop such activities on the part of mass media. Previous moves against covertly pro-Kremlin media have sparked outrage and accusations of attacks on the freedom of speech. If applied in the run-up to elections, this will be interpreted as the use of administrative leverage.
RELATED ARTICLE: Deliberately undecided: Who will influence the result of the 2019
It will be equally difficult to restrict disinformation on social media, even if some have announced campaigns to counter fake news and bot accounts. Instagram and Facebook are momentarily removing videos showing Russian oligarchs entertain themselves, yet they are in no rush to close numerous separatist communities.
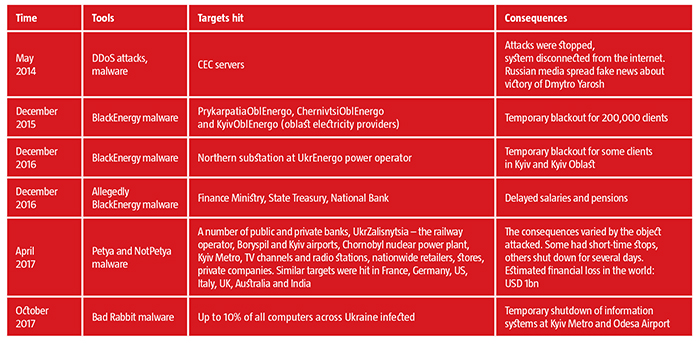
The third likely card will be cyber influence. This is a fairly affordable tool as one attack can cost up to several thousand dollars, yet it takes experienced experts to carry out. Still, this will be a popular tool as proven by hacker interference with the 2014 presidential election in Ukraine. That incident pushed information security specialists to disconnect Central Electoral Commission servers from the internet after some Russian TV channels had used the fake image of the Right Sector’s Dmytro Yarosh that appeared on CEC computers to talk of his victory in the election. The skills of Russian cyber criminals were not the only element of that attack. One of the planned stages in spreading the malware to affect CEC computers was the involvement of a CEC employee who had to copy the virus and insert it into the system through a memory card.
Who is in charge?
According to Valentyn Petrov, Head of the Information Security Department at the National Security and Defense Council, says that technical protection of information, including cyber protection, is the responsibility of the owner. In the case of Ukraine’s election, the owner is the Head of the Central Electoral Commission. Therefore, CEC Head is in charge of the Elections Unified Information & Analytical System, its elements and channels of communication. “This is an axiom. The law states so, and the owner is always responsible for attacks on any objects of critical infrastructure,” he notes.
Poor protection leads to penalties under Art. 363 of the Criminal Code. This provision lists penalties for violations in the use of computers, networks or systems. A hacker attack thus puts responsibility on two parties – the hackers involved and the head of the organization or institution who failed to set up proper protection of his or her information resources.
Despite a number of powerful cyberattacks with serious consequences that have taken place in Ukraine, there have been no reports on penalties for the leaders of these institutions who failed to keep up with the standards of protection. The norms and standards are developed by the Special Communication and Information Service (SCIS). It is also in charge of inspecting the compliance with these standards at various institutions.
According to Petrov, the results of the voting will be protected by other security entities apart from CEC and SCIS. Past practices have proven the efficiency of setting up working groups with technical experts from CEC, SCIS, Security Bureau of Ukraine and National Police. This mechanism has been tested in previous elections, and Ukraine has managed to hold two elections even in the difficult circumstances as the war unfolded.
RELATED ARTICLE: What threats face Ukraine if a fragmented Verkhovna Rada is elected?
Also, Petrov believes that hackers would not be able to actually affect the results of the voting if their attack on CEC succeeded. In Ukraine, all votes are counted by hand, on paper ballots and protocols, while electronic systems largely serve for informative and consulting purposes. The winner would thus be determined even if the CEC were to shut down or show distorted results.
Its security is further reinforced by the fact that most of CEC’s information resources, including the Elections or Presidential Elections systems, are in a suspended mode and launched a few weeks before the voting begins. As they go into operation, a complex of information protection is created and trainings are conducted to model potential threats. This takes place at central units and district election commissions. The timeframe of security inspection normally matches the official start and end of the election process.
The State Register of Voters can be another target of the cyber criminals. Unlike most of CEC’s resources, it operates on a permanent basis. It contains identification data on the voters, their personal data with places and terms of the voting, and service data. Whoever has access to this resource can hypothetically affect the voting at separate territorial units. This will hardly affect the elections overall. But this type of activity has at least one dangerous element — interference with this resource can undermine the accuracy of the elections. Therefore, they can be recognized illegitimate.
Then any candidate or political party can claim that they have lost elections because of cyberattacks, not poor public support. This is a convenient excuse as average voters will hardly have tools to check how accurate such claims are. News under such headlines can ruin trust in any of the potential winners.
The Law on the State Register of Voters defines the register manager as the one responsible for protecting it – the integrity and accuracy of its databases, as well as correct operation of equipment and software – alongside SCIS. They are responsible for preventing attempts of illegal intrusion, copying or elimination of information. Also, the law establishes legal responsibility for violations of the register protection procedure through unauthorized access, violation of integrity, copying and deletion. According to Andriy Mahera, CEC Deputy Head, CEC is now managing the State Register of Voters, as prescribed by law. Therefore, it is qualified CEC departments that provide the protection of the register’s information resources in cooperation with the SBU and SCIS. When it comes to potential threats, Mahera says that no system in the world is 100% hackerproof. Still, he believes that interference with CEC systems unlikely.
It is widely distributed and operates across the territory of Ukraine. It is impossible to hide at one protected premises. So every section of it is individually vulnerable to external intrusions. However, interference with lower sections provides very limited access to the main servers. This makes these attacks less significant.
RELATED ARTICLE: How Ukraine's political talk shows work
As a result, hackers are most likely to focus on the CEC’s central servers based in Kyiv. “We are much better prepared for such situations,” Petrov notes. He believes that Ukraine’s authorities realize how serious the threats are and prepare to counter them.
Sean Townsend, spokesman for the Ukrainian Cyber Alliance, an activist cyber-security group, agrees. He says that state entities should be better prepared for the elections after the 2014 attacks, so CEC servers will not be as vulnerable as other government resources. He says that there are currently no visible vulnerabilities or hacks in the CEC’s information resources that could be examined by activists without violating the law. Still, he believes that other government entities involved in the election process can end up being attacked by the criminals. So can the media for the purpose of spreading misleading information. “We have to prepare for information and combined attacks in advance,” Townsend comments. In his view, cyber security of government resources – CEC systems included – can be improved through personal responsibility of employees for the data and systems they are in charge of. Equally important is exchange of information between experts in government and the private sector. “This should not work as instructions given from above or as statements from press services, but as initiatives on the lower levels,” Townsend says. Government entities need to have system operators interested in preserving data, while cyber security entities should help them and make their work easier rather than threaten them with punishment and control.
Petrov claims that there are some issues with the legislative base hampering cooperation between government and private entities. Most laws have been drafted for the public sector. The Law on the Foundations of Cyber Security was the only breakthrough, but it has not yet come into effect. It outlines the obligations of the owners of critical infrastructure objects, public or private, for information protection.
Yet, the culture of employees and their perception of threats, especially in government entities, remain the key element of cyber security. Petrov mentions a recent campaign by Ukrainian Cyber Alliance where the activists looked for critical vulnerabilities in information systems at public entities and crucial national enterprises, and reported on them. “We can draft any law and build any system of protection, open centers and set up protected networks. But none of this will work if the human factor remains weak,” he comments.
The clock is ticking
As to technical details, Petrov talks about a national telecommunications network that has been created in Ukraine and is being developed now to deliver secure connection and transfer of data for public entities. This network provides sufficient protection of information, including cryptography. Ukraine is one of the few countries that have a full cycle of cryptography production of their own. Over the time left until the elections, it has to construct the system of protection. The National Cyber Security Coordination Center is working to that end under the National Security and Defense Council. As this article was going to press, the upcoming meeting of the Center planned to discuss the protection of CEC information resources.
“We know our weak spots. We have identified those who will build the system, the infrastructure they will use and the software solutions they will apply. We are working in advance to avoid any rush,” Petrov comments on the preparations. According to the SBU, its representatives have implemented a new model to counter the threats to seamless work of CEC resources in cooperation with SCIS and CEC, and with support of some top IT companies in Ukraine. One of the elements is a tenfold backup of communication channels for CEC systems. SBU representatives have noted that all automated e-systems of the CEC operate with a comprehensive information protection system authorized by the SCIS.
To speed up information exchange on cyber attacks, a national computer emergency response team (CERT) is being built. International practices show that some specific systems benefit from own centers. Ukraine already has a CERT-UA headquarters. Specialized teams have been created at the SBU, the National Bank and the Ministry of Energy. A separate center is underway for the General Staff of the Armed Forces. A number of initiatives are developing in the private sector. “If we have 10-15 centers operating and exchanging data in real time, it will make our cyber security system far more resilient,” Petrov claims. According to Townsend, cyber centers are a necessary element of the national security system. Still, the problem he sees is in a lack of proper communication among them and insufficient understanding of the challenges in this sector. He believes that public entities and enterprises must learn to interact between themselves, with society and cyber centers.
The latest election trends in the world prove that politics and the IT tools involved in it grow more sophisticated and damaging. Ukraine is likely to face an entire range of new tools used to lead pro-Kremlin political forces to power or to decrease the share of pro-European ones in power. Agents of influence, kompromat and fake information, as well as DDoS attacks against CEC make an additional front in the hybrid war against Ukraine. 2019 will show how resilient it is.
Translated by Anna Korbut
Follow us at @OfficeWeek on Twitter and The Ukrainian Week on Facebook

